This step by step guide will outline the stages to setup a Remote Desktop Services (RDS)deployment with Server 2012 R2. This platform will allow access to either full Remote Desktop or Remote App sessions via a load balanced set of Session Hosts. Windows Server 2012 gives you several options that offer you the ability to automatically distribute the application icons to users, and even keeps them up to date if later on you make some changes to what apps (and desktops!) are available through RDS. The RDWeb Access web site; The RemoteApp control panel; Through Group Policy.
This step by step guide will outline the stages to setup a Remote Desktop Services (RDS)deployment with Server 2012 R2.
This platform will allow access to either full Remote Desktop or Remote App sessions via a load balanced set of Session Hosts. Access will be available via Remote Desktop Gateway, Remote Desktop Web Access or via the Start Menu using RemoteApp and Desktop Connections.
Environment
To standardise the guide for use in other networks, an internal domain name of fabrikam.local and an external domain name of contoso.com will be assumed. All servers are running Server 2012 R2 Standard.
Design
The following roles will be installed on one server, RDS01: Remote Desktop Connection Broker, Remote Desktop Licensing, Remote Desktop Gateway and Remote Desktop Web Access. A further two servers, RSH01 and RSH02 will host the Remote Desktop Session Host role.
Pre-requisites
One public IP address is required for use with inbound traffic to the Remote Desktop Web, Gateway and Connection Broker roles. A certificate covering apps.contoso.com, broker.contoso.com and gateway.contoso.com will be installed on RDS01. Split DNS should be configured on internal DNS servers for the contoso.com zone. As this deployment assumes an non publicly routable internal domain name the Connection Broker will be installed in Highly Available mode to allow it to have a custom DNS name in contoso.com. This configuration requires the use of a SQL database accessed via the SQL Native Client. This can be avoided if your internal domain name matches your external domain name.
Servers
Start by building RDS01, RSH01 and RSH02 as per your server build processes. The servers used in this guide are up to date with all Important Windows Updates.
DNS
Create the DNS entries for contoso.com in both internal and external DNS
| Type | Name | Value |
| A | broker.contoso.com | External DNS: Public IP Address / Internal DNS: LAN IP of RDS01 |
| A | gateway.contoso.com | As above |
| A | apps.contoso.com | As above |
| TXT | _msradc | https://apps.contoso.com/RDWeb/Feed/webfeed.aspx |
Firewall
Forward TCP Ports 80 + 443 and UDP 3391 to RDS01
Active Directory
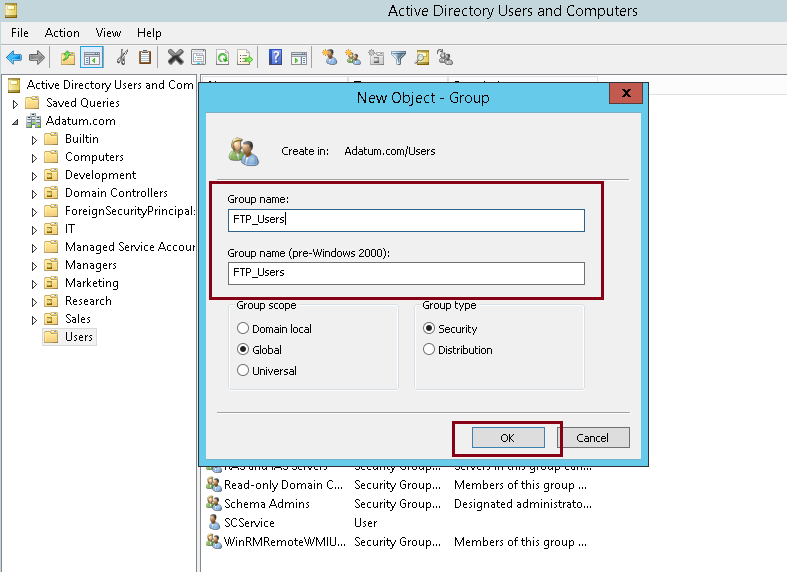
Create the following Security Groups:
Remote Desktop Connection Brokers Members: RDS01
Remote Desktop Gateway Users Members: User Accounts and/or Groups of Users authorised to connect via RD Gateway
RemoteApp <appname> Members: User Accounts and/or Groups of Users authorised to use particular Remote App
Group Policy
Target Users:
Policies>Administrative Templates>Windows Components>Remote Desktop Services>Remote App and Desktop Connections Specify default connection URL: https://apps.contoso.com/rdweb/feed/webfeed.aspx
Target Computers:
Policies>Administrative Templates>Windows Components>Remote Desktop Services>Remote Desktop Connection Client Specify SHA1 thumbprints of certificates representing trusted .rdp publishers: Thumbprint of RD Connection Broker Publishing certificate.
Target Session Hosts:
Policies>Administrative Templates>Windows Components>Remote Desktop Services>Remote Desktop Session Host>Licensing Specify the licensing mode for the RD Session Host server: Per User Use the specified Remote Desktop license servers: RDS01.fabrikam.local.
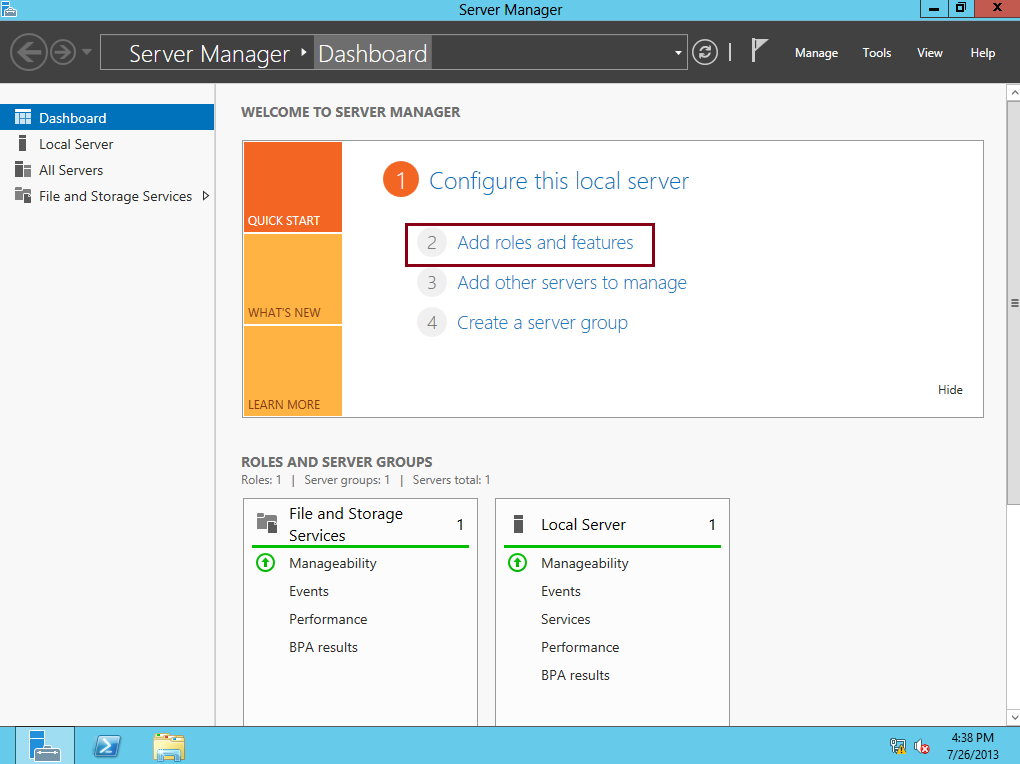
Setup the Deployment
Open Server Manager on RDS01 and in the Dashboard section click Add other servers to manage. Find RSH01 and RSH02 and add them to the selection on the right hand side. Click Add roles and features, select Remote Desktop Services installation, Standard Deployment then Session-based desktop deployment. Continue through the wizard and select RDS01 for the RD Connection Broker and RD Web Access roles. Select RSH01 and RSH02 for the RD Session Host role. Confirm the choices in the Completion then click Deploy. Open Remote Desktop Services from Server Manager and click the green plus to install RD Gateway. Select the RDS01 server then enter gateway.contoso.com for the certificate name. Close the wizard upon completion. The certificate and other settings will be configured later. Click the green plus to install RD Licensing and select RDS01 as the target server.
Open the Remote Desktop Licensing Manager from Administrative Tools. Expand the All servers entry then right click RDS01 and click Activate Server. Complete the activation wizard as per your licensing arrangement. Ensure the computer account for RDS01 is in the Terminal Server License Servers group in Active Directory.
Create a SQL login for the Remote Desktop Connection Brokers security group with the dbcreator Security Role. Install the SQL Native Client which can be found on the installation media used to install SQL. From the Remote Desktop Services dashboard in Server Manager, right click RD Connection Broker and select Configure High Availability. The connection string will vary depending on the environment but for SQL 2008 R2, this should work assuming a SQL server name of SQL01:
DRIVER=SQL Server Native Client 10.0;SERVER=SQL01;Trusted_Connection=Yes;APP=Remote Desktop Services Connection Broker;DATABASE=RDCB
Enter a path for the database relative to the target SQL Server e.g. C:Program FilesMicrosoft SQL ServerMSSQL10_50.MSSQLSERVERMSSQLDATA. The DNS round robin name will be broker.contoso.com. If the wizard fails to complete, check the SQL server logs for errors. For the error Token-based access validation failed with an infrastructure error, restart RDS01 to update it's computer account security group membership following its addition to the Remote Desktop Connection Brokers security group.
Click Tasks in the Deployment Overview section then Edit Deployment Properties. Confirm the RD Gateway server name is gateway.contoso.com. Set the RD Licensing mode as per your environment and confirm the server choice. Import the certificate one entry at a time clicking Apply after each one. Import from a .pfx file containing the private key.
Open the Remote Desktop Gateway Manager from Administrative Tools. Modify the existing Connection Authorization Policy so that only members of the Remote Desktop Gateway Users group are allowed. In the Resource Authorization Policies section, click Manage Local Computer Groups and create a group named Remote Desktop Gateway Group. On the Network resources tab, add the following names: RSH01.fabrikam.local, RSH02.fabrikam.local, apps.contoso.com, broker.contoso.com. Modify the existing Resource Authorization policy to use the Remote Desktop Gateway Group on the Network Resource tab.
Certain changes can only be made via PowerShell. For any errors, try running PowerShell as admin. First import the Remote Desktop module with Import-Module RemoteDesktop. To change the Connection Broker round robin name use Set-RDClientAccessName -ConnectionBroker RDS01.fabrikam.local -ClientAccessName broker.contoso.com. The default Workspace Name seen when logging into RD Web Access is Work Resources. This can be changed with Set-RDWorkspace -Name 'Contoso'.
Open IIS Manager from Administrative Tools and drill down to the Default Web Site and open HTTP Redirect. Tick Redirect requests to this location and enter the URL as https://apps.contoso.com/rdweb. Set the status code to Permanent (301) then apply the changes. From the Default Web Site, Drill down to RDWeb then Pages and open Application Settings. Set the value of DefaultTSGateway to gateway.contoso.com. To remove the Connect to a Remote PC option from RD Web Access, set the value of ShowDesktops to false.
At this point, we have a functional Remote Desktop Services Platform. Before creating a Session Collection, let's review what we have:
Users can access Remote Apps and Desktops in the following ways:
Open apps.contoso.com and get automatically redirected to the secure Remote Desktop Web interface. After logging in with domain credentials, users are presented with icons representing Remote Desktop and Remote App programs.
Add Remoteapp Server 2012 Sp2
For domain joined machines running Windows 8, the configured group policy will automatically connect to the web feed and display Remote Desktop and Remote App programs. Windows 7 machines will need to be manually connected. Users can either enter the full webfeed URL (https://apps.contoso.com/rdweb/feed/webfeed.aspx) or, due to the DNS TXT record, enter an email address ending @contoso.com. Icons can be found in the RemoteApp and Desktop Connections program folder in the Start Menu.
For non domain joined machines, users can manually connect their computer to the web feed in one of two ways: Entering the full web feed URL or entering their email address assuming the email address suffix matches the domain name where the DNS TXT record was created. After entering domain credentials, they can access Remote Desktop and Remote App programs in the same way as domain joined machines.
The Remote Desktop Connection Broker will load balance incoming connections across all Session Hosts in a Session Collection. If a user has a disconnected session, the broker will reconnect them to it.
Remote Desktop Gateway is utilised in the background but it can also be used directly. The configuration detailed above restricts access via RD Gateway to only those names required to access Session Collections. If needed, this restriction can be relaxed to allow connection to internal computers via standard Remote Desktop tunneled through SSL by RD Gateway. The RD Gateway Server should be configured as gateway.contoso.com and Windows 7 machines should install the latest Remote Desktop Connection Client to enable Web SSO (Single Sign On). Direct connections to computers can also be made via the RD Web interface using the Connect to a Remote PC option.
Creating a Session Collection
A Session Collection will by default present a full Remote Desktop environment. When choosing a name, keep in mind this will be visible to users in the following places: The RemoteApp and Desktop Connections program folder Start Menu and the RD Web interface. Create the collection from Server Manager>Remote Desktop Services>Collections>Tasks>Create Session Collection. User Profile Disks allow User Profiles to be stored by Remote Desktop Services in per user VHDX files. This allows user profile data to persist if sessions move between Session Hosts in the collection. Assign at least two Session Hosts to the Collection for load balancing and redundancy. Once created, an icon will be visible in the Start Menu and RDWeb interface with the same name as the Collection.
If additional Collections are created, keep in mind that a Session Host can only be part of one Collection. Also, a Collection can either present full desktop sessions or Remote Apps, not both.
To use Remote App, install an application onto each Session Host in the Collection. From Server Manager>Remote Desktop Services open the Collection then click Tasks>Publish RemoteApp Programs from the RemoteApp Programs section. If an application isn't detected, it can be manually added to the list. Tick any required applications then click Next and Publish. Once applications are published to the Collection, it will no longer present full desktop sessions. Also, the Collection Name isn't visible anywhere. Programs delivered via Remote App, appear as locally installed applications which run from a hidden Remote Desktop session.
Once published to the Collection, right click the application and edit its properties. Modify the User Assignment to restrict access to the previously created group if required.
Testing
Confirm the following things to check the Deployment is setup correctly: From a domain joined Windows 8 machine, open RemoteApp and Desktop Connections and confirm it has been automatically connected via Group Policy. From a domain joined Windows 7 machine, open RemoteApp and Desktop Connections. Test connecting to the deployment via both the Web Feed URL and by using an email address. From a non domain joined machine external to the network, connect to http://apps.contoso.com and confirm the redirect to HTTPS occurs. Login to RD Web using Domain Credentials and check the icons for Remote Desktops or RemoteApps are present. Open either a Remote Desktop or RemoteApp and check that from a domain joined machine, there is no warning that a website is trying to run a RemoteApp program. The warning will show for non domain joined machines unless the same group policy option is set manually in the Local Security Policy. Confirm that the Remote Desktops or RemoteApps open. If the Connect to a Remote PC option hasn't been disabled, confirm it can be used to connect to an internal workstation/server. The RD Gateway computer group may need to be updated to allow this. Confirm a connection can be made using Remote Desktop Gateway outside of RD Web. Use the monitoring section of RD Gateway to confirm that connections to the deployment are using UDP.
Remote Desktop Services Roaming User Profiles
In a multi Session Host deployment, users will end up with local profiles on each one. If any applications require configuration that is stored in the profile, centralising the profiles will prevent the need to duplicate this configuration as user sessions are load balanced across the hosts. Outlook is a good example.
If you have roaming user profiles already, there may be no need to setup separate RDS roaming profiles and the decision on where to store them will be specific to your infrastructure. Although the profile path can be set at the user account level, it can also be set by Group Policy. The second policy listed below, if required, should be set on the Session Hosts and not the server where the profiles are stored as it is the Session Host that will create the folder.
Target Session Hosts:
Policies>Administrative Templates>Windows Components>Remote Desktop Services>Remote Desktop Session Host>Profiles
Set path for Remote Desktop Services Roaming User Profile
Policies>Administrative Templates>System>User Profiles
Add the Administrators security group to roaming user profiles: Enabled
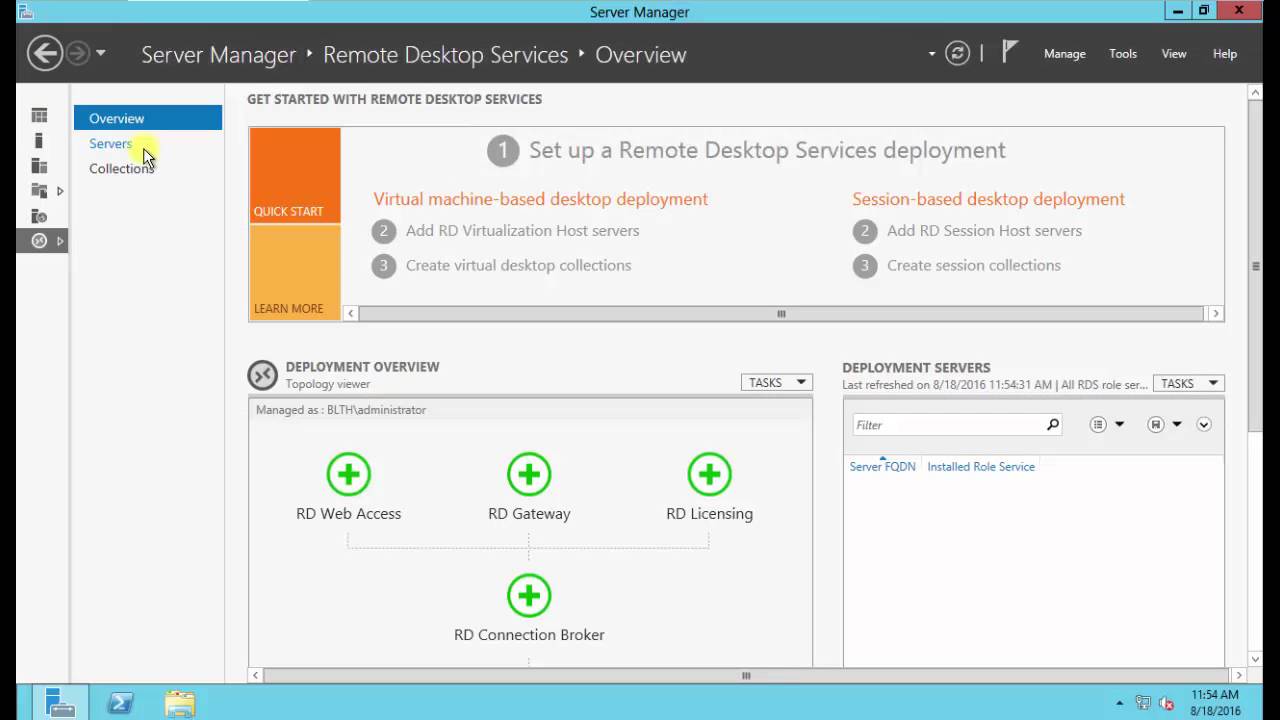
Setup High Availability
To provide redundancy for the deployment, the Connection Broker, Web Access, Gateway and Licensing roles should be configured for High Availability. Prepare another server named RDS02 and on RDS01, add it to Server Manager via Add other servers to manage from the Dashboard.
In this example, the Connection Broker is already configured in High Availability mode so most of the hard work is done already. Add the computer account for RDS02 to the Remote Desktop Connection Brokers security group and install the SQL Native Client as with RDS01. Open SQL Management Studio on the server with the RDCB database and under Security>Logins, open the properties for the Remote Desktop Connection Brokers group. Under User Mapping, tick the RDCB database and assign db_owner permission. From the Deployment Overview on RDS01, right click the RD Connection Broker icon and click Add RD Connection Broker Server. Complete the wizard selecting RDS02 as the target server. Install the RD Web Access and Gateway roles on RDS02 in the same manner by right clicking their icons in the Deployment Overview. The Remote Desktop Gateway configuration will need to be copied from RDS01. Unless any other changes have been made, just match the default RD CAP and RAP policies.
Currently, the apps, broker and gateway DNS records point internally and externally via NAT to the IP of RDS01. DNS Round Robin is no longer supported as Remote Desktop Gateway in Server 2012 R2 requires IP affinity. Windows Network Load Balancing or a similar mechanism should be used. Once in place, update the internal DNS records and external NAT rules to point to the Virtual IP of the load balancing mechanism.
Assuming per user mode with RD Licensing, the easiest method to provide redundancy is to add the Licensing role to RDS02 and then Activate it. In per user mode, each Session Host only requires connectivity to an activated server. In the event of a permanent loss of RDS01, the licenses can be added to RDS02. Update the group policy to include RDS02 in the list of license servers set on the Session Hosts.
This completes the setup of High Availability for the Remote Desktop Services Deployment.
We hope you have found this useful!
RemoteApp in Windows Server 2012R2
To use Remote App on Windows Server 2012 R2, the server must be connected to a domain for RemoteApp to work (this was not a requirement in 2008 R2). See link below, in 2012 R2 (but not 2012), Active Directory can be on the same server as RD Connection Broker.
http://blogs.msdn.com/b/rds/archive/2013/07/09/what-s-new-in-remote-desktop-services-for-windows-server-2012-r2.aspx — See this section: “Single server RDS deployment including Active Directory. We now support running our RD Connection Broker role service on the same physical instance as an Active Directory Domain Controller. In addition, we published guidelines for how RD Session Host could be used without the RD Connection Broker.”
Ways to Distribute RemoteApps in Windows Server 2012 R2:
http://social.technet.microsoft.com/wiki/contents/articles/14488.distribution-of-remote-apps-and-desktops-in-windows-server-2012.aspx — “Distribution of Remote Apps and Desktops in Windows Server 2012”
1) Distribute using RD Web Access – similar to how it was done in 2008 R2 by going to your site: http://IPofSERVER/rdweb
http://technet.microsoft.com/en-us/library/ee216776.aspx 2008R2Access RemoteApp and Desktop Connection by Using the RD Web Access Web Site
http://technet.microsoft.com/en-us/library/cc731508.aspx 2008R2 Connect to Remote Desktop Web Access
2) Distribute using Web Feed URL in the control panel – In 2008R2, you could create .rdp files using RemoteApp Wizard but that has been replaced in 2012 and the Web Feed method is recommended.
http://social.technet.microsoft.com/wiki/contents/articles/14488.distribution-of-remote-apps-and-desktops-in-windows-server-2012.aspx — Distribution of Remote Apps and Desktops in Windows Server 2012
Another approach (which isn’t specific to RemoteApp) is to create remote desktop shortcuts – see video on our website – http://www.riptidehosting.com/Dedicated-Server-Configuration-Videos.aspx These shortcuts can be made regardless of remote app but users have the ability to edit them.
Additional Links relating to 2012 RDS:
http://technet.microsoft.com/en-us/library/hh831447.aspx – remote desktop services overview for 2012
Microsoft Remoteapp Server
http://social.technet.microsoft.com/wiki/contents/articles/10817.publishing-remoteapps-in-windows-server-2012.aspx – Publishing RemoteApps in 2012
Remoteapp Server 2012 R2
http://blogs.technet.com/b/windowsserver/archive/2012/05/09/windows-server-2012-remote-desktop-services-rds.aspx – Windows Server 2012 Remote Desktop Services (RDS) on windows server blog